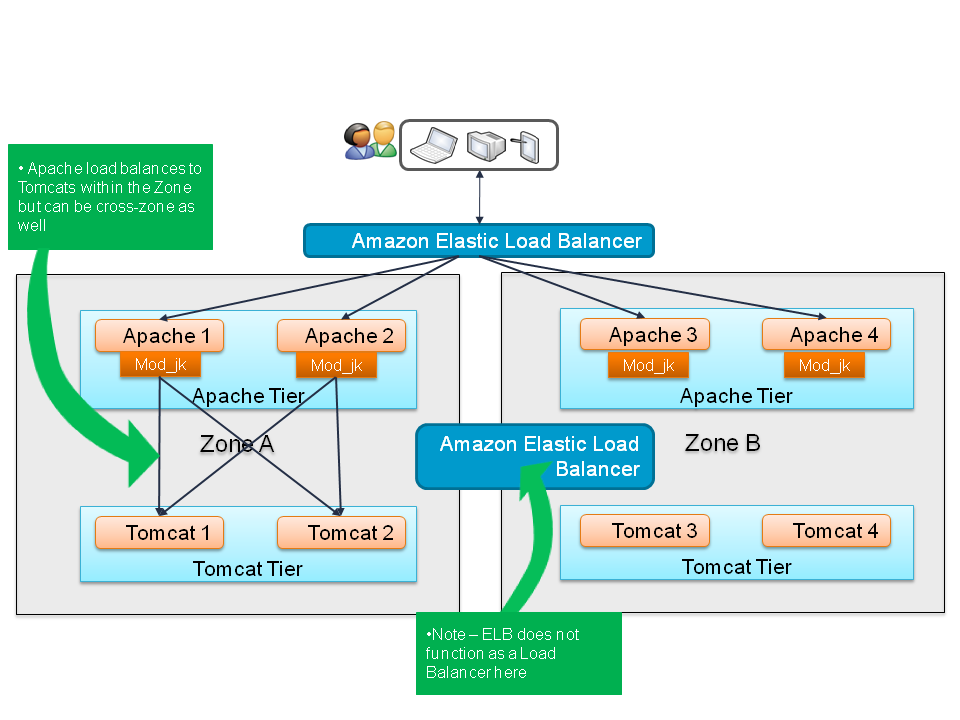
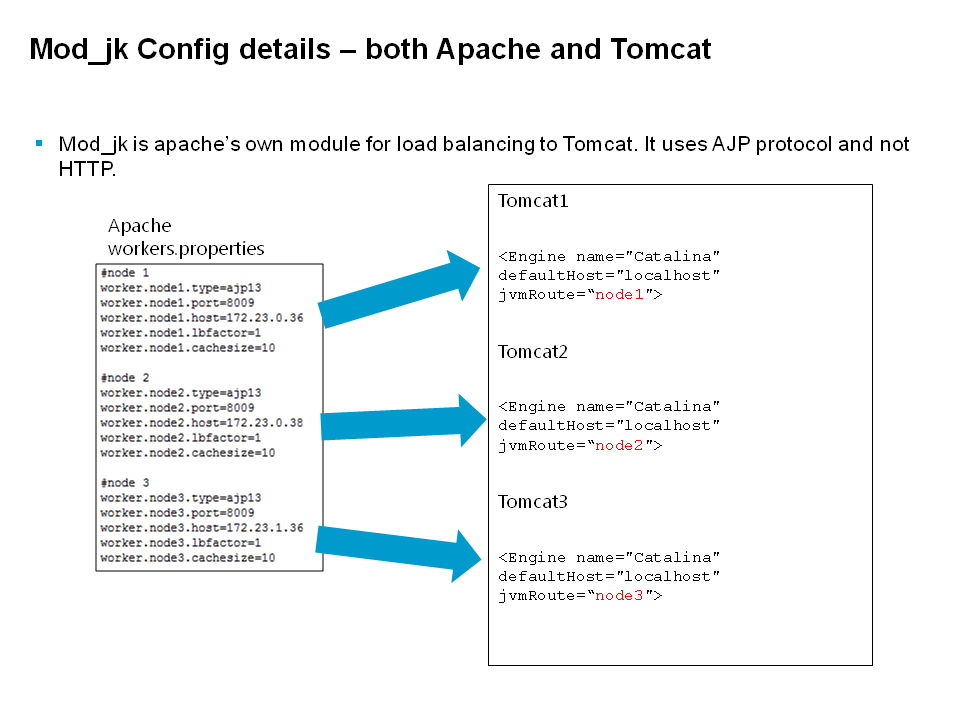
Due to the limitation with mod_jk for autoscaling configurations, we took a look at mod_proxy
ProxyPass /css !
ProxyPass /media !
So if you need a single Tomcat per JVM then this is the best solution.
For multiple JVMs there is an alternate recommendation given to us by Amazon support, and that is to use one ELB per port and set up the tomcat tier with multiple ELBs as shown below.
This will work provided you allocate the architecture and resources in the right manner.
Instead of
using AJP (mod_jk) protocol we can use the HTTP protocol and with this approach we do not
use Apache for the actual load balancing or session stickiness. Instead all requests from
the Apache server are forwarded to the application tier ELB (say it runs at HTTP port 8080) and
the ELB does load balancing as well as maintains session stickiness.
The
Apache httpd.conf configuration for the same is mentioned below.
LoadModule proxy_module modules/mod_proxy.so
LoadModule proxy_http_module modules/mod_proxy_http.so
ProxyPass /img !
ProxyPass /images !ProxyPass /css !
ProxyPass /media !
ProxyPass /
http://internal-RCCL-AppTier-ELB-722360436.us-east-1.elb.amazonaws.com:8080/
ProxyPassReverse /
http://internal-RCCL-AppTier-ELB-722360436.us-east-1.elb.amazonaws.com:8080/
§Pros:
–ELB is able to maintain sticky sessions using it’s own
cookie named AWSELB
§Cons:
–When we need to run multiple Tomcat JVMs on the same instance,
this approach fails. For eg: If we have 6 Tomcats distributed as Server 1 on ports
8080, 8085, 8090 and Server 2 on ports 8080, 8085, 8090. In this case, on
Apache we need to switch to mod_proxy_balancer and Apache will load balance across 3 ELBs running
on 8080, 8085 and 8090 respectively.
–In such a scenario, session stickyness
fails again as it again requires the same combination of unique node names (jvmRoutes)
for each Tomcat instances and these need to be pre-defined on Apache as well.
So we face the same issue on mod_jk See http://stackoverflow.com/questions/9393163/apache-tomcat-problems-with-sticky-sessions-and-load-balancing
For multiple JVMs there is an alternate recommendation given to us by Amazon support, and that is to use one ELB per port and set up the tomcat tier with multiple ELBs as shown below.
This will work provided you allocate the architecture and resources in the right manner.